Highlights
- Cyber risk quantification (CRQ) provides a structured and objective methodology for quantifying cyber risk, moving beyond qualitative assessments to inform strategic security decisions.
- By offering a data-driven approach to risk prediction and forecasting, CRQ empowers organizations to proactively address potential cyber threats and optimize their security investments.
- A CRQ framework will help organizations understand the financial impact of cyber risks, facilitating informed resource allocation and prioritization of mitigation efforts.
On this page
The CRQ imperative
In today’s escalating cyber threat landscape, the imperative for cyber risk quantification (CRQ) and its relevance for the C-Suite has become undeniably clear.
‘You can’t manage what you can’t measure’—this enduring principle, attributed to leading business consultant Peter Drucker, underscores the fundamental role of robust and effective measurement in achieving successful management outcomes. Traditionally, organizations have gauged cyber risk based on qualitative and often subjective scales, employing terms such as ’high’, medium’, and ’low’. Cyber risk quantification (CRQ) introduces a paradigm shift to this approach by applying quantifiable metrics and measurable values to cyber risks, moving beyond the limitation of purely qualitative assessments.
The contemporary threat landscape
With escalating geopolitical tensions, uncertain environments, digital growth, and rapid adoption of emerging technologies, the threat vectors and cyber landscape have drastically changed. This has led to an increase in:
- Number of worldwide cyber attacks
- Cybercrime remediation costs
- Global cyber insurance premiums
Through this, it is evident that managing cyber risk effectively and efficiently needs to be a top priority for all organizations, looking to navigate this complex and uncertain environment.
CRQ enhances your ability to anticipate and prepare for cyber risks, ultimately improving your resilience against cyber threats. It provides you with a consistent and comparable way to measure and assess risks. This helps you make informed decisions about cyber security risk management. CRQ is also used in calculating the return on investment for cybersecurity measures.
Structured, objective process to analyze risks
CRQ provides organizations with a structured and objective methodology for designing, implementing, and managing quantitative risk analysis.
This independent, flexible, and scalable framework that builds on the FAIR (factor analysis of information risk) methodology facilitates the alignment of historical risk assessments and the generation of ongoing residual risk calculations.
CRQ involves the rigorous evaluation and measurement of an organization's cybersecurity risks with mathematical modelling techniques, such as the Monte Carlo simulation and binomial distribution. By assigning a financial value to the potential impact of each risk, CRQ enables informed resource allocation for mitigation initiatives. The process encompasses the identification of developing risk scenarios, the estimation of loss and event frequency and impact, and the articulation of risk in structured quantitative terms to facilitate decision-making. CRQ plays a crucial role in risk prediction and forecasting by providing a data-driven approach to comprehend potential cyber threats and their associated mitigation costs.
Barriers and solutions
To understand the transformative potential of a CRQ engine, it is crucial to first acknowledge the inherent barriers in the traditional risk management practices.
The CRQ framework offers an effective solution to tackle the challenges that traditional methods pose, helping organizations be more proactive with their security strategy (see Figure 1).
CRQ in action
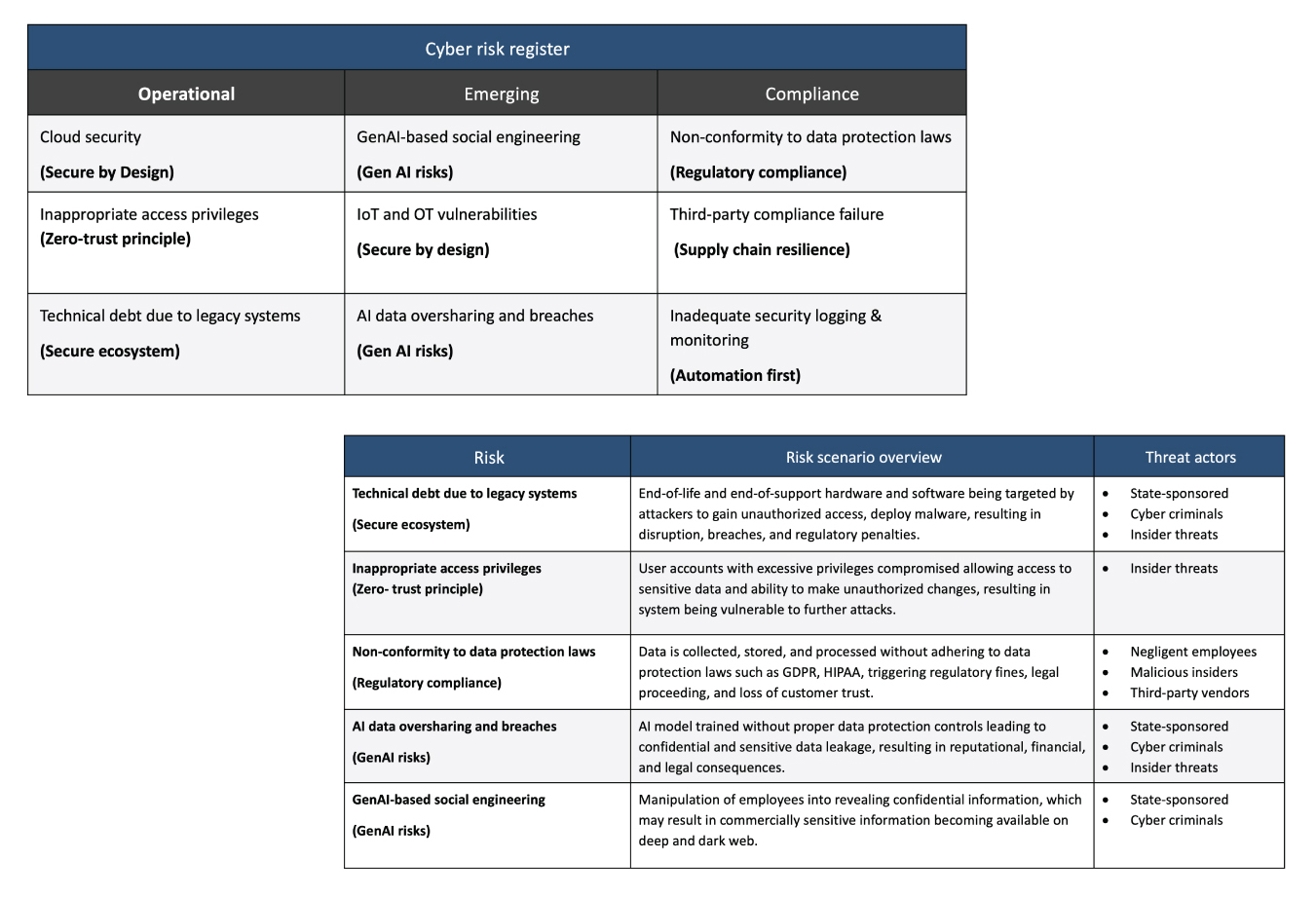
A typical CRQ journey starts with the cyber risk register.
The risk register will traditionally capture the organization’s top risks.
Operational |
Emerging |
Compliance |
Cloud security |
GenAI-based social engineering (GenAI risks) |
Non-conformity to data protection laws (Regulatory compliance) |
Inappropriate access privileges (Zero-trust principle) |
IoT and OT vulnerabilities (Secure by design) |
Third-party compliance failure (Supply chain resilience) |
Technical debt due to legacy systems (Secure ecosystem) |
AI data oversharing and breaches (GenAI risks) |
Inadequate security logging & monitoring (Automation first) |
Table 1: Cyber risk register
Diving deeper into the risks reveals the next layer, ie, scenario planning. Scenario planning allows you to view your risks in greater detail and identify the key threat actors and types.
Risk scenario overview |
Threat actors |
|
Technical debt due to legacy systems (Secure ecosystem) |
End-of-life and end-of-support hardware and software being targeted by attackers to gain unauthorized access, deploy malware, resulting in disruption, breaches, and regulatory penalties. |
|
Inappropriate access privileges (zero- trust principle)
|
User accounts with excessive privileges compromised allowing access to sensitive data and ability to make unauthorized changes, resulting in system being vulnerable to further attacks. |
|
Non-conformity to data protection laws (Regulatory compliance) |
Data is collected, stored, and processed without adhering to data protection laws such as GDPR, HIPAA, triggering regulatory fines, legal proceedings, and loss of customer trust. |
|
AI data oversharing and breaches (GenAI risks) |
AI model trained without proper data protection controls leading to confidential and sensitive data leakage, resulting in reputational, financial, and legal consequences. |
|
GenAI-based social engineering (GenAI risks) |
Manipulation of employees into revealing confidential information, which may result in commercially sensitive information becoming available on deep and dark web. |
|
Table 2: Scenario planning
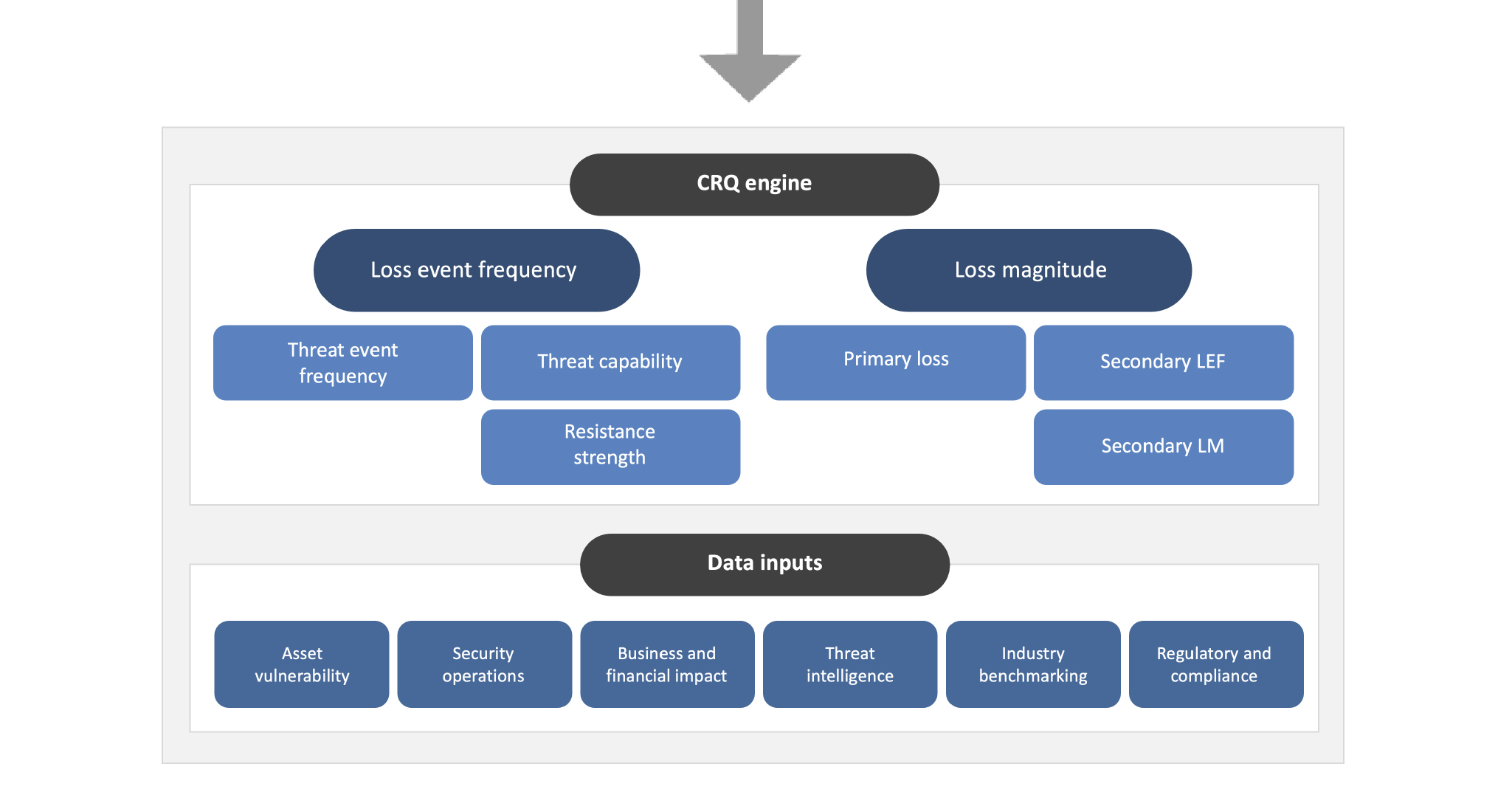
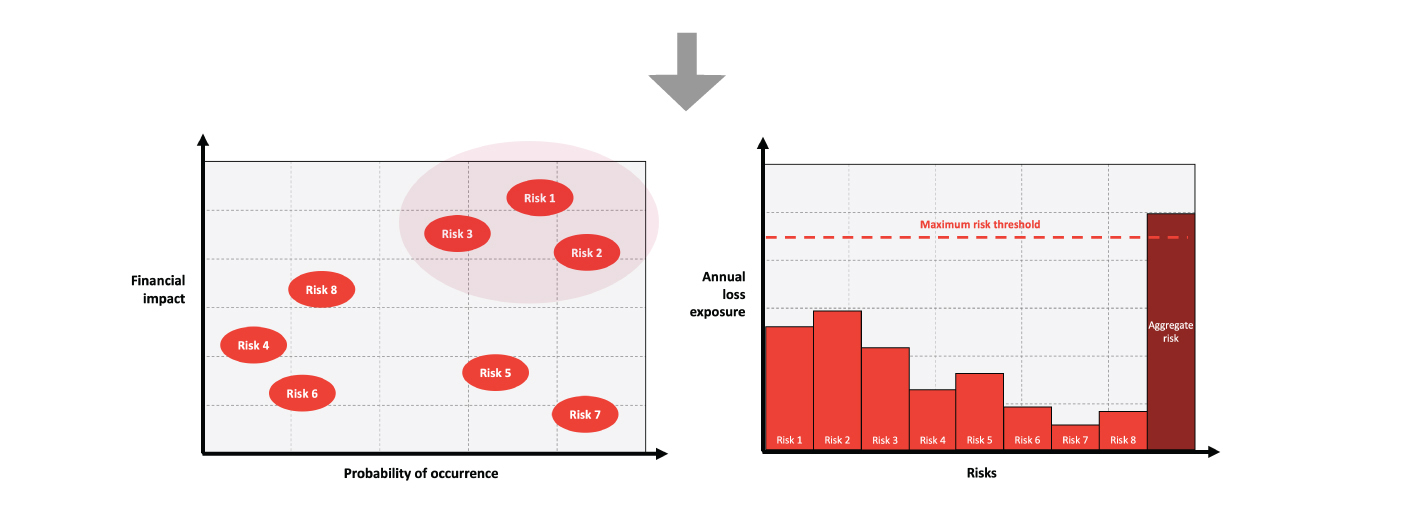
For the purposes of illustration on how you can deploy CRQ, we have shown a high-level example below. The TCS CRQ engine (based on the Open Fair Methodology) uses your existing risk register and risk scenarios and combines that with internal and external data sources to calculate and compare the cost profile of your risks. Data inputs such as threat intelligence and industry benchmarks make the overall outputs rich and comprehensive to give appropriate financial loss value to each risk.
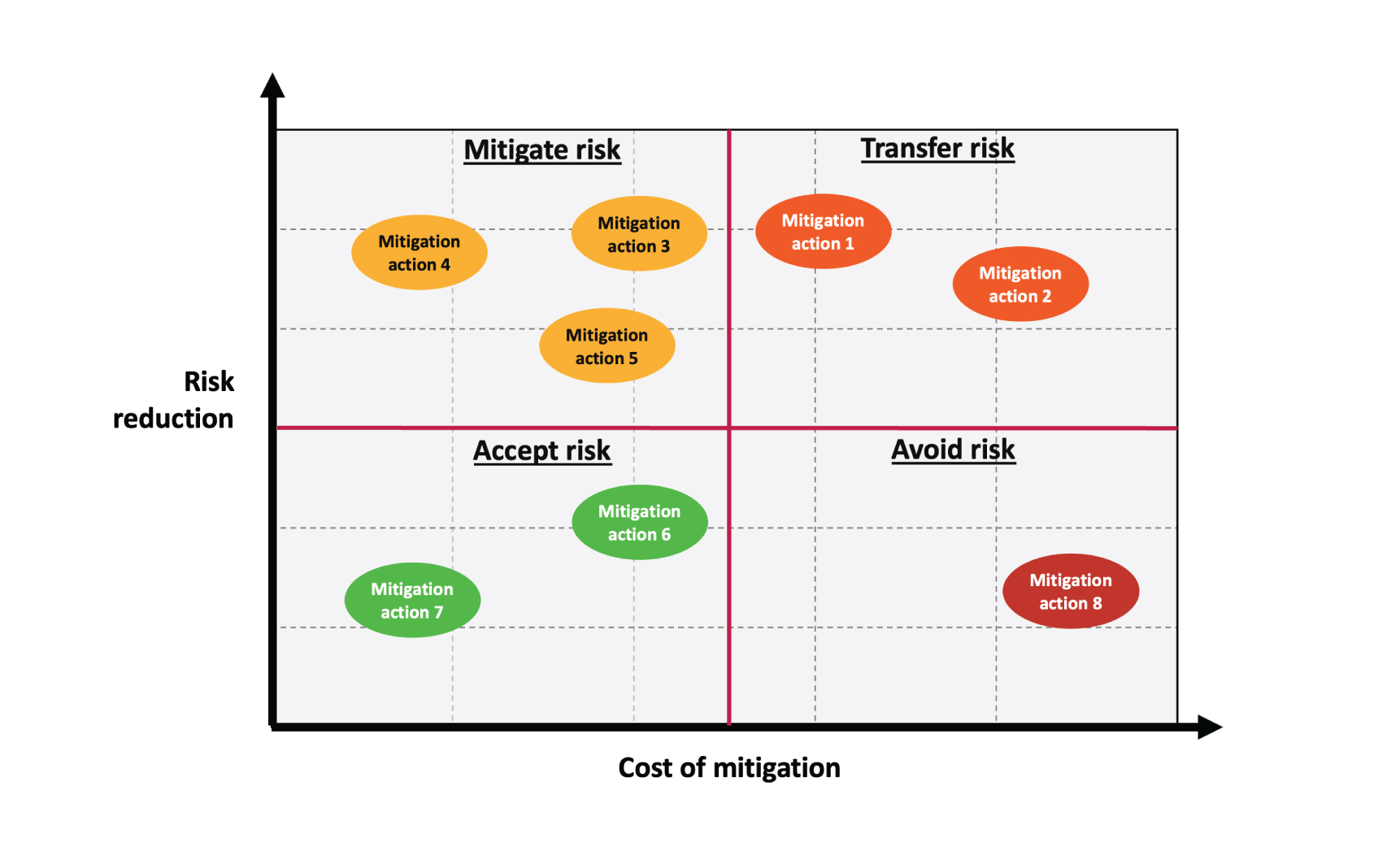
The outputs from the CRQ engine can be utilized to manage the risk and select appropriate mitigation treatment, which will ensure cybersecurity investments are made where they are needed the most.
Benefits of CRQ
CRQ empowers organizations to make more informed decisions and strengthen their overall cybersecurity posture.
The several advantages of CRQ include:
- Informed, focused decision-making: CRQ enables organizations to prioritize cybersecurity investments by quantifying the potential financial impact of cyber risks. This data-driven approach provides assurance to the board and allows for strategic allocation of resources to mitigate the most significant threats.
- Optimal allocation of resources: By understanding the financial implications of various cyber risks, organizations can allocate their resources more effectively. CRQ facilitates the identification of critical tasks and ensures that the maximum resources are directed towards areas where they will have the greatest impact in reducing potential losses.
- Improved risk impact communication: CRQ facilitates clear and concise communication of cyber risks in financial terms. This allows security teams to effectively convey the potential business impact to executives, board members, and other stakeholders who may not be familiar with technical cybersecurity jargon, fostering better understanding and support for security initiatives.
- Enhanced regulatory compliance: Implementing CRQ provides a structured approach to risk assessment and reporting, ensuring that the organization meets relevant regulatory requirements. The quantifiable nature of CRQ can provide stronger evidence of due diligence and risk management efforts.
- Strategic cyber insurance: A robust CRQ framework allows organizations to leverage their effective governance mechanisms to potentially manage and optimize cyber insurance premiums. By demonstrating a clear understanding and quantification of their cyber risks, organizations may be able to secure more favorable insurance terms.
Guidelines for an effective CRQ approach
A robust CRQ that moves beyond subjective assessments empowers organizations to achieve true cyber resilience.
An effective approach should ensure:
- Strategic CRQ alignment: CRQ strategies should be tailored to your unique objectives, making it a foundation for informed security investments.
- Enhanced CRQ capability: The CRQ engine should integrate with your existing platforms to automate analysis, scoring, and prioritization.
- Cultivating a CRQ-aware culture: Targeted training across all levels is a must to foster data-driven security.
- Optimizing CRQ operations: Managed services will help provide a consistent, reliable solution for risk quantification and treatment comparison.
Transform your cybersecurity with the power of CRQ.